Home >> Uncategorized >> Computer intrusion forensics research paper
Computer intrusion forensics research paper
Apr/Tue/2017 | Uncategorized
Computer Forensics - US-Cert pdf

Advances in Computer Forensics - paper ijcsns… -… pdf

Computer Forensics - US-Cert pdf
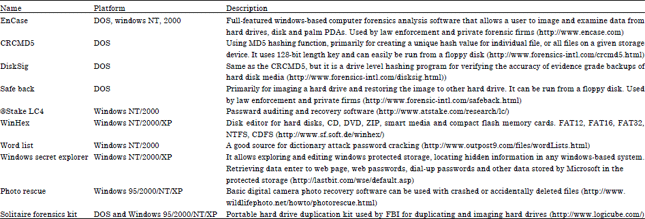
Computer Intrusion Forensics Research Paper - Nathan… pdf
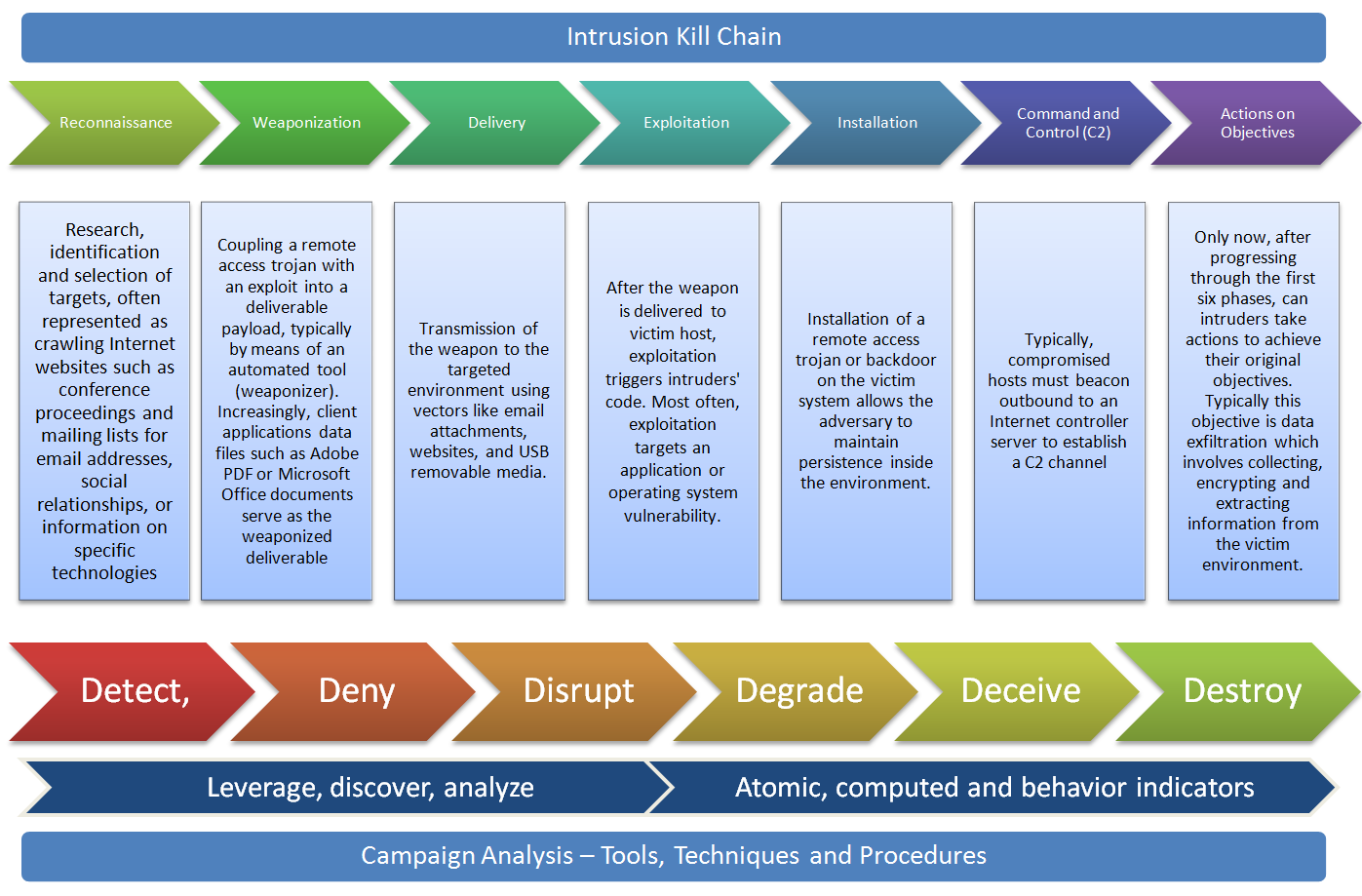
Computer Intrusion Forensics Research Paper - Nathan… pdf

Digital forensics - Wikipedia

Computer Intrusion Forensics Research Paper - Nathan… pdf

Digital forensics - Wikipedia

Plethora of Cyber Forensics - The Science and Information… pdf

Digital forensics - Wikipedia

Methods for Using Intrusion Logs to Establish Criminal…

Tools And Technology For Computer Forensics:… pdf

Research On Some Relevant Problems in Computer… pdf

Tools And Technology For Computer Forensics:… pdf

Tools And Technology For Computer Forensics:… pdf

Computer and Intrusion Forensics pdf -… pdf

Computer and Intrusion Forensics pdf -… pdf

Methods for Using Intrusion Logs to Establish Criminal…

Advances in Computer Forensics - paper ijcsns… -… pdf

Methods for Using Intrusion Logs to Establish Criminal…
